Red Teaming
Red teaming is the combative process of relentlessly criticizing plans, procedures, procedures, and preconceptions. A red team can be a contractual independent party or an internal group that employs techniques to foster an outsider viewpoint.

Red Team Operations
Sectechs provides Red Team Security Testing for enterprises, which includes all of the key modules (5), which can be increased based on the needs of the company. The majority of the work done during red team operations is black box penetration testing.
“Sectechs team start testing from phase 1 and make it to phase 5 of penetration testing”
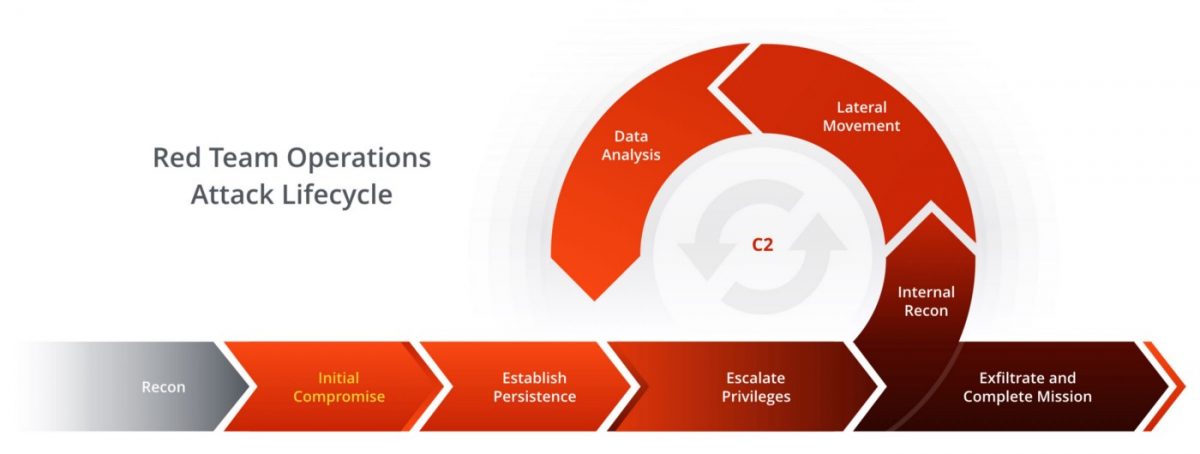
The purpose of doing Red Team operations is to ensure that the company is not compromised and will not be compromised by any attack, as well as to determine if the business is adhering to security requirements for risk and threat assessments.

