Malware Analysis
- Static
- Dynamic
- Hybrid
- Static
- Dynamic
- Hybrid
Types of Malwares
A trojan is a form of malware that hides its actual substance in order to trick the consumer into believing it is a safe file.
The following are some of the most prevalent forms of Trojan viruses:
» Backdoor Trojans
» Exploit Trojans
» Rootkit Trojans
» Downloader Trojans
Ransomware is a type of malware that is always developing and is meant to lock data on a machine, leaving any data and the methods that depend on them inoperable. Malicious hackers will then demand a ransom to unlock the data.
Ransomware having many families i.e. (Cerber, Sodinokibi, Babuk, Ryuk and Mailto)
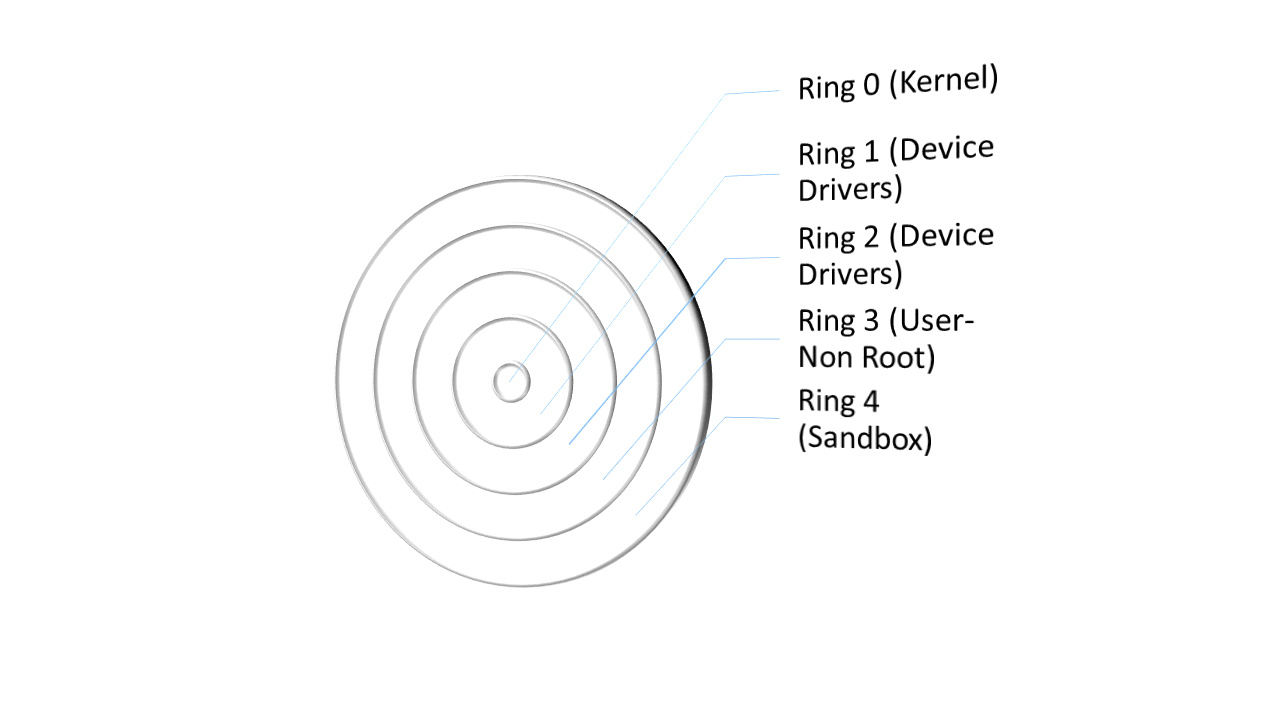
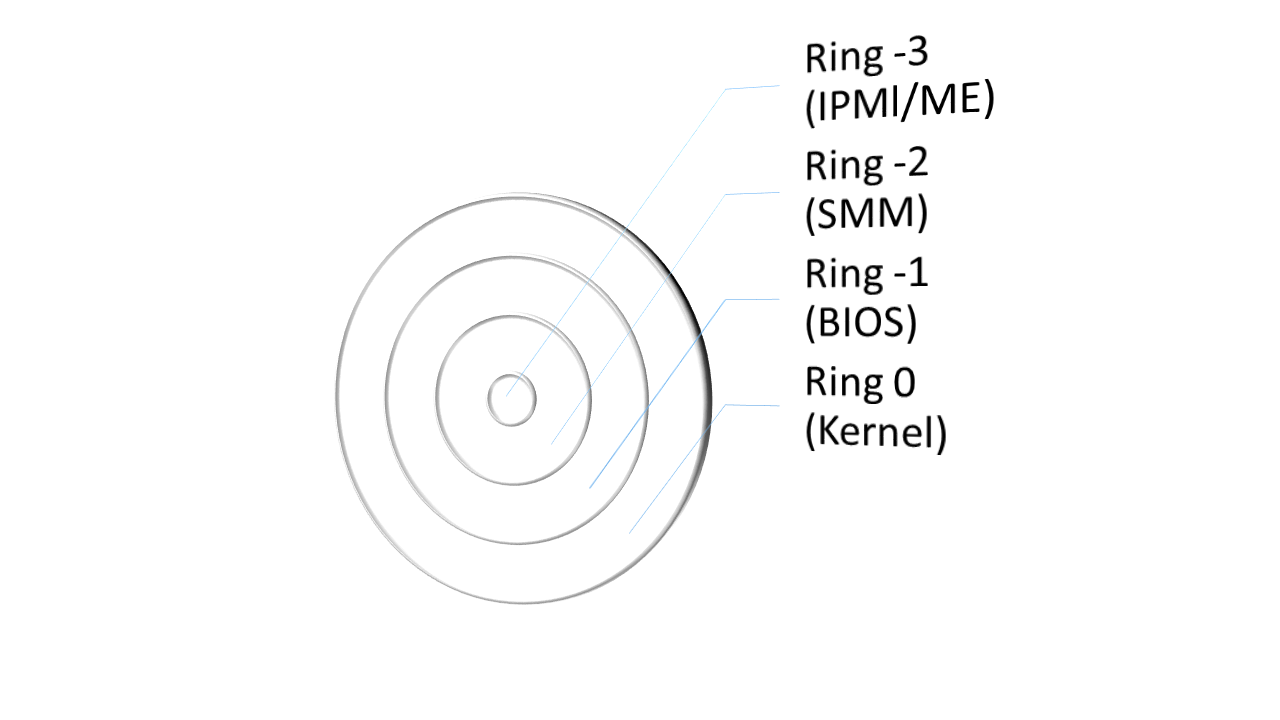
A rootkit is a covert computer software that is meant to maintain elevated computer access but actively concealing its operation. The phrase rootkit is derived from the terms “root” and “kit.” Traditionally, a rootkit was a suite of techniques that granted administrators access to a machine or networks.
Rootkit Types
- User-mode or application rootkit
- Memory rootkit
- Bootloader rootkit or Bootkit
- Hyper-V rootkits
- Hardware or firmware rootkit
- Kernel rootkit
Keyloggers, often known as keystrokes trackers, are software applications or physical hardware that monitor keypad activity (keys pushed). Keylogging software are a type of malware in which consumers are clueless that their activities are being recorded.
Fileless malware is a form of malicious code that infects a machine via infiltrating normal apps. Which does not use files and leaves no trace, making it difficult to identify and delete.
Malware Analyst Professional
» Basic Understanding of Programming Languages (Python, .NET, C/C++)
» Basic Understanding of User mode debugging
» Basic Understanding of File formats and structures
- Introduction to Debuggers
- Fundamentals for Static and Dynamic Analysis
- Basic Principles for Reverse Engineering
- IDA Pro and Ghidra maneuvers
- x86 and x64 assembly for reversing
- Reversing PE files and DLL
- Understanding the Process injection of malware
- Fundamentals of cryptography for malwares
- C# and Java code obfuscation to readable code
- Understanding File compression code with reversing
- Methodologies to analyzed Fileless malware
- Demonstration of complete malware reversing (Ransomware)
Malware Analyst Expert
» Good Knowledge of Kernel and User Mode Debugging
» Virtualization hands-on experience
» Basic Understanding Operating System APIs (Win)
» dnSpy hands-on experience
» Malware Analyst Professional (Recommended)
- Reversing Anti-Debugger Malwares
- Understanding Injection/Using Windows API by malwares
- Analysis of Shellcode/Exploit into PDF/RTF Files
- Reversing Packed and Unpacked Malware Files
- Reversing Fileless Malware
- Finding the Correct Kill-Switch from malware
- Understanding rootkits pattern from Ring 3 to Ring 0
- Python for Malware Detection
- Understanding Hardware Malware (Hardware Trojans)


